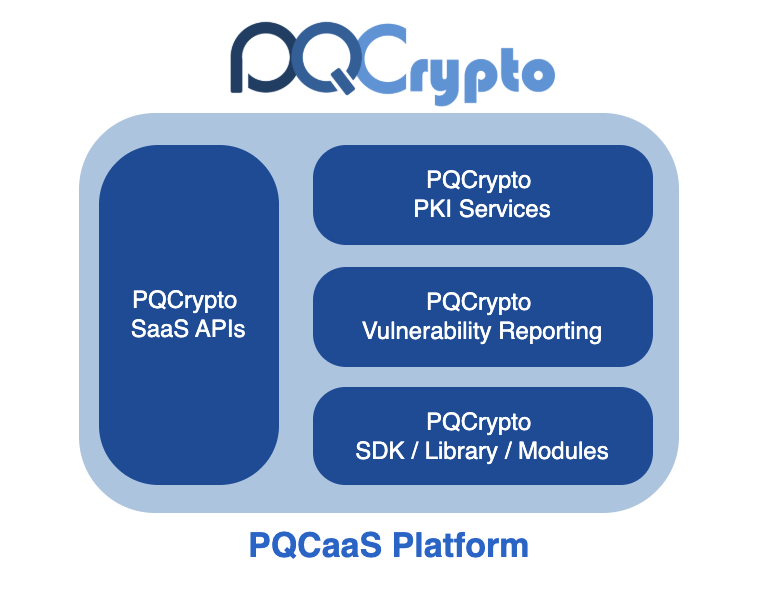
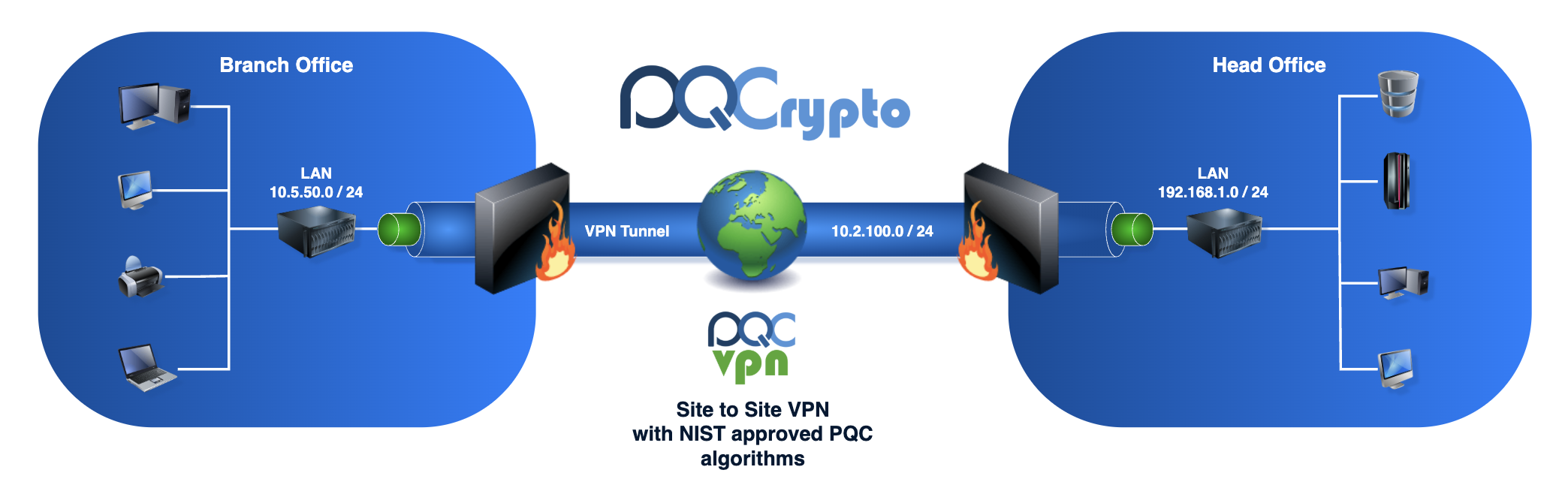
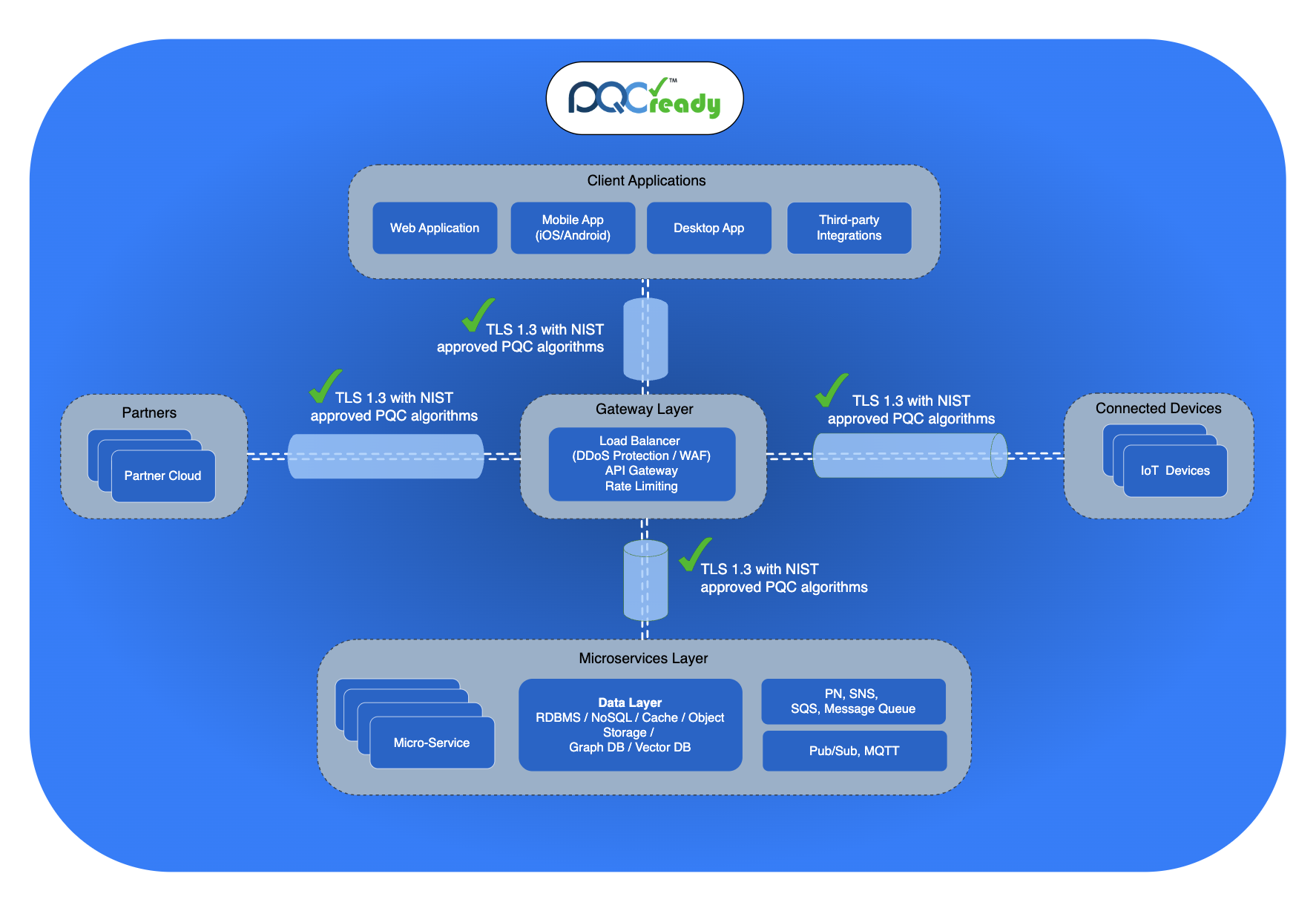
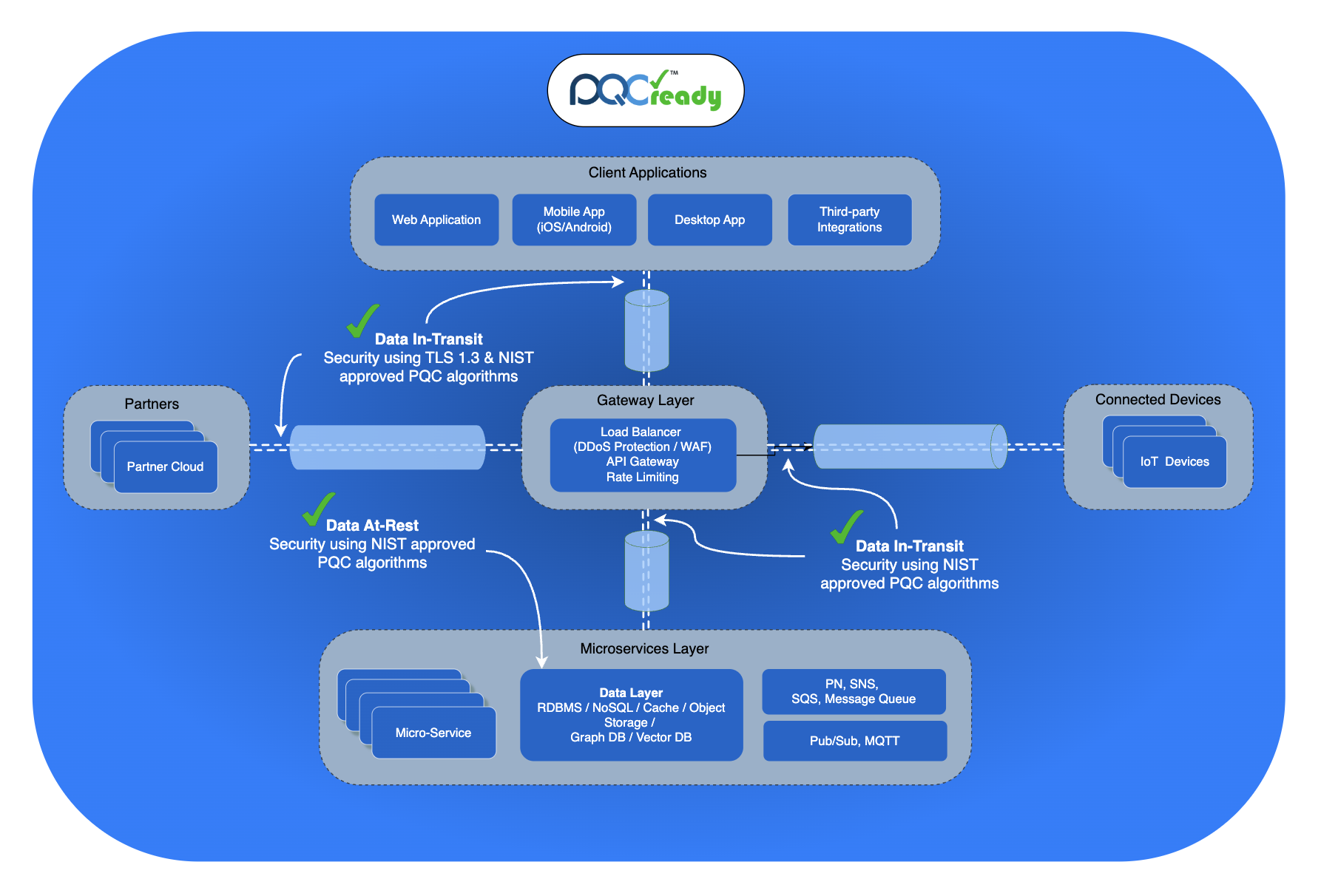
Future-Proof Your Cryptographic Infrastructure
Transition to quantum-resistant cryptography with confidence. Our comprehensive PQC solutions protect your data against the quantum threat while maintaining compatibility with existing systems.
Why Post-Quantum Cryptography Matters
Quantum computers pose an existential threat to current cryptographic systems. RSA, ECC, and Diffie-Hellman—the foundation of today's internet security—will be broken by sufficiently powerful quantum computers.
The threat is real and imminent. "Harvest now, decrypt later" attacks are already happening, where adversaries collect encrypted data today to decrypt it once quantum computers become available. Organizations must act now to protect their long-term sensitive data.
Store Now, Decrypt Later
Adversaries are harvesting encrypted data today for future decryption
Regulatory Compliance
Governments worldwide are mandating and guiding post-quantum cryptography (PQC) migration, with U.S. federal agencies expected to transition between 2025 and 2035
 ?
?